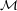 =
= 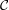 =
=  = {0,…,25}. Define
= {0,…,25}. Define
YALE UNIVERSITY
DEPARTMENT OF COMPUTER SCIENCE
| CPSC 467b: Cryptography and Computer Security | Handout #4 | |
| Professor M. J. Fischer | February 8, 2010 | |
Problem Set 2
Due on Monday, February 15, 2010
In this problem set, we consider a variant of the Caesar cipher which we call the “Happy-2010” cipher
(named after the venerable “Happy Hacker” of CPSC 223 fame). Happy-2010 (E,D) is defined as follows:
Let 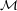 =
= 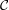 =
=  = {0,…,25}. Define
= {0,…,25}. Define
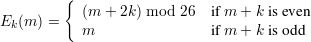
We also consider Double Happy (E2,D2). Here,  2 =
2 =  ×
× , and E(k1,k2)2 = Ek1(Ek2(m)).
, and E(k1,k2)2 = Ek1(Ek2(m)).
Feel free to write programs to help you solve these problems. If you do, include the programs and their output along with your solutions, and say how the computer was used.
Problem 1: Happy Encryption (5 points)
Encrypt the plaintext “i am a secret message” using Happy with key k = 3. (As usual, we will ignore spaces.)
Problem 2: Happy Decryption (5 points)
Describe the Happy decryption function Dk(c).
Problem 3: Security (10 points)
Problem 4: Equivalent Key Pairs (10 points)
Suppose m0 = c0 = 4.
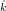 ,
,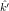 )2(m0) =
E(k,k′)2(m0) = c0, does E(
)2(m0) =
E(k,k′)2(m0) = c0, does E(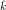 ,
,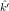 )2(m) = E(k,k′)2(m) for all m
)2(m) = E(k,k′)2(m) for all m 
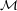 ? Why or why not?
? Why or why not?Problem 5: Group Property (10 points)
Is Happy a group? Why or why not?