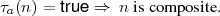
YALE UNIVERSITY
DEPARTMENT OF COMPUTER SCIENCE
| CPSC 467a: Cryptography and Computer Security | Notes 10 (rev. 1.1) | |
| Professor M. J. Fischer | October 10, 2006 | |
Lecture Notes 10
Formally, a test of compositeness is a set T = {τ1,…,τs}, where τi : Z →{true, false} has the property that
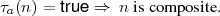
If τa(n) = true, we say that τa(n) succeeds, and a is a witness to the compositeness of n. If τa(n) = false, then the test fails and gives no information about the compositeness of n. Clearly, if n is prime, then all τa fail on n, but if n is composite, then τa(n) may either succeed or fail.
A test of compositeness T is useful if there is a feasible algorithm T(n,a) that computes τa(n), and for every composite number n, a fraction c > 0 of the tests succeed on n. Suppose for simplicity that c = 1∕2 and one applies 100 randomly-chosen tests to n. If any of them succeeds, we have a proof that n is composite. If all fail, we don’t know whether or not n is prime or composite. But what we do know is that if n is composite, the probability that all 100 tests fail is only 1∕2100.
In practice, what we do to choose RSA primes p and q is to choose numbers at random and apply some fixed number of randomly-chosen tests to each candidate,1 rejecting the candidate if it proves to be composite. We keep the candidate (and assume it to be prime) if all of the tests for compositeness fail. We never know whether or not our resulting numbers p and q really are prime, but we can adjust the parameters to reduce the probability to an acceptable level that we will end up a number p or q that is not prime (and hence that we have unknowingly generated a bad RSA key).
Here are two examples of tests for compositeness.
 Z is a valid test of compositeness.
Unfortunately, it isn’t very useful in a probabilistic primality algorithm since the number of
tests that succeed when n is composite are too small. For example, if n = pq for p,q prime,
then the only tests that succeed are δp and δq.
Z is a valid test of compositeness.
Unfortunately, it isn’t very useful in a probabilistic primality algorithm since the number of
tests that succeed when n is composite are too small. For example, if n = pq for p,q prime,
then the only tests that succeed are δp and δq.
 Z is a valid test of compositeness. For this test
to be adequate for a probabilistic primality algorithm, we would need to know that for all
composite numbers n, a significant fraction of the tests ζa succeed on n. Unfortunately, there
are certain compositeness numbers n called pseudoprimes for which all of the tests ζa fail.
Such n are fairly rare, but they do exist. The ζa tests are unable to distinguish pseudoprimes
from true primes, so they are not adequate for testing primality.
Z is a valid test of compositeness. For this test
to be adequate for a probabilistic primality algorithm, we would need to know that for all
composite numbers n, a significant fraction of the tests ζa succeed on n. Unfortunately, there
are certain compositeness numbers n called pseudoprimes for which all of the tests ζa fail.
Such n are fairly rare, but they do exist. The ζa tests are unable to distinguish pseudoprimes
from true primes, so they are not adequate for testing primality.We will return to this topic later when we have developed sufficient number theory to present tests of compositeness that do have the properties needed to make them useful in probabilistic primality algorithms.
We now return to a basic result of number theory that will be used later.
Let n1,n2,…,nk be positive pairwise relatively prime positive
integers2 ,
let n = ∏
i=1kni, and let ai  Zi for i = 1,…,k. Consider the system of congruence equations with
unknown x:
Zi for i = 1,…,k. Consider the system of congruence equations with
unknown x:
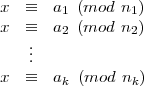 | (1) |
The Chinese Remainder Theorem says that (1) has a unique solution in Zn.
To solve for x, let
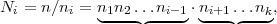
and compute Mi = Ni-1 mod ni, for 1 ≤ i ≤ k. Note that Ni-1 (mod ni) exists since gcd(Ni,ni) = 1 by the pairwise relatively prime condition. We can compute Ni-1 using the methods of section 46 (lecture notes 9). Now let
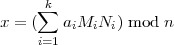 | (2) |
If j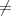 i, then MjNj ≡ 0 (mod ni) since ni∣Nj. On the other hand, MiNi ≡ 1 (mod ni) by definition of
Mi. Hence,
i, then MjNj ≡ 0 (mod ni) since ni∣Nj. On the other hand, MiNi ≡ 1 (mod ni) by definition of
Mi. Hence,
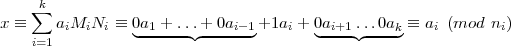 | (3) |
for all 1 ≤ i ≤ k, establishing that (2) is a solution of (1).
To see that the solution is unique in Zn, let χ be the mapping x (x mod n1,…,x mod nk). χ is a
surjection3
from Zn to Zn1 ×…× Znk since we have just shown for all (a1,…,ak)
(x mod n1,…,x mod nk). χ is a
surjection3
from Zn to Zn1 ×…× Znk since we have just shown for all (a1,…,ak)  Zn1 ×…× Znk that there exists
x
Zn1 ×…× Znk that there exists
x  Zn such that χ(x) = (a1,…,ak). Since also ∣Zn∣ = ∣Zn1 ×…×Znk∣, χ is a bijection, and (1) has only
one solution in Zn.
Zn such that χ(x) = (a1,…,ak). Since also ∣Zn∣ = ∣Zn1 ×…×Znk∣, χ is a bijection, and (1) has only
one solution in Zn.
The bijection χ is interesting in its own right, for it establishes a one-to-one correspondence between members of Zn and k-tuples (a1,…,ak) in Zn1 ×… × Znk. This lets us reason about and compute with k-tuples and then translate the results back to Zn.
The homomorphic property of χ means that performing an arithmetic operation on x  Zn corresponds
to performing the similar operation on each of the components of χ(x). More precisely, let ⊙ be
one of the arithmetic operations +, -, or ×. If χ(x) = (a1,…,ak) and χ(y) = (b1,…,bk),
then
Zn corresponds
to performing the similar operation on each of the components of χ(x). More precisely, let ⊙ be
one of the arithmetic operations +, -, or ×. If χ(x) = (a1,…,ak) and χ(y) = (b1,…,bk),
then
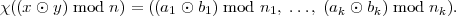 | (4) |
In other words, if one first performs z = (x ⊙ y) mod n and then computes z mod ni, the result is the same as if one instead first computed ai = (x mod ni) and bi = (y mod ni) and then performed (ai ⊙ bi) mod ni. This relies on the fact that (z mod n) mod ni = z mod ni, which holds because ni∣n.
In section 42 (lecture notes 8), we showed that RSA decryption works when m,c  Z*n but omitted the
proof that it actually works for all m,c
Z*n but omitted the
proof that it actually works for all m,c  Zn. We now use the Chinese Remainder Theorem to supply this
missing piece.
Zn. We now use the Chinese Remainder Theorem to supply this
missing piece.
Let n = pq be an RSA modulus, p,q distinct primes, and let e and d be the RSA encryption and
decryption exponents, respectively. We show med ≡ m (mod n) for all m  Zn.
Zn.
Define a = (m mod p) and b = (m mod q), so
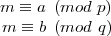 | (5) |
Raising both sides to the power ed gives
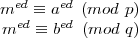 | (6) |
We now argue that aed ≡ a (mod p). If a ≡ 0 (mod p), then obviously aed ≡ 0 ≡ a (mod p). If a ⁄≡ 0
(mod p), then gcd(a,p) = 1 since p is prime, so a  Z*p. By Euler’s theorem,
Z*p. By Euler’s theorem,
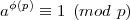
Since ed ≡ 1 (mod φ(n)), we have ed = 1 + uφ(n) = 1 + uφ(p)φ(q) for some integer u. Hence,
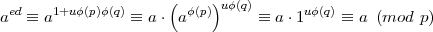 | (7) |
Similarly,
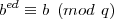 | (8) |
Combining the pair (6) with (7) and (8) yields
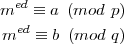
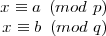 | (9) |
From (5), m is also a solution of (9). By the Chinese Remainder Theorem, the solution to (9) is unique modulo n, so med ≡ m (mod n) as desired.
Several possible attacks on RSA are discussed below and their relative computational difficulties discussed.
The security of RSA depends on the computational difficulty of several different problems, corresponding to different ways that Eve might attempt to break the system. The first of these is the RSA factoring problem: Given a number n that is known to be the product of two primes p and q, find p and q. Clearly if Eve can find p and q, then she can compute the decryption key d from the public encryption key e (in the same way that Alice did when generating the key) and subsequently decrypt all ciphertexts.
Eve doesn’t really need to know the factors of n in order to compute d. It is enough for her to know φ(n). Computing φ(n) is no harder than factoring n since φ(n) is easily computed given the factors of n, but is it perhaps easier? If it were, then Eve would have a possible attack on RSA different from factoring n. It turns out that it is not easier, for if Even knows φ(n), then she can factor n. She simply sets up the system of quadratic equations
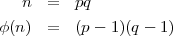
Another possibility is that Eve might somehow be able to compute d from e and n even without the ability to factor n or compute φ(n). That would represent yet another attack that couldn’t be ruled out by the assumption that the RSA factoring problem is hard. However, that too is not possible, as we now show.
Suppose Eve knows n and e and is somehow able to obtain d. Then Eve can factor n by a probabilistic algorithm. The algorithm is presented in Figure1.
We begin by finding unique integers s and t such that 2st = ed- 1 and t is odd. This is always possible
since ed - 1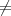 0. One way to find s and t is to express ed - 1 in binary. Then s is the number of trailing
zeros and t is the value of the binary number that remains after the trailing zeros are removed. Since
ed - 1 ≡ 0 (mod φ(n)) and 4∣φ(n) (since both p - 1 and q - 1 are even), it follows that
s ≥ 2.
0. One way to find s and t is to express ed - 1 in binary. Then s is the number of trailing
zeros and t is the value of the binary number that remains after the trailing zeros are removed. Since
ed - 1 ≡ 0 (mod φ(n)) and 4∣φ(n) (since both p - 1 and q - 1 are even), it follows that
s ≥ 2.
Now, for each a chosen at random from Z*n, define a sequence b0,b1,…,bs, where bi = a2it mod n, 0 ≤ i ≤ s. Each number in the sequence is the square of the number preceding it modulo n. The last number in the sequence is 1 by Euler’s theorem and the fact that φ(n)∣(ed - 1). Since 12 mod n = 1, every element of the sequence following the first 1 is also 1. Hence, the sequence consists of a (possibly empty) block of non-1 elements, following by a block of 1’s.
It is easily verified that b0 is the value of b when the innermost while loop is first entered, and bk is the value of b after the kth iteration of that loop. The loop executes at most s- 1 times since it terminates just before the first 1 is encounter, that is, when b2 ≡ 1 (mod n). At this time, b = bk is a square root of 1 (mod n).
Over the reals, we know that each positive number has two square roots, one positive and one negative,
and no negative numbers have real square roots. Over Z*n for n = pq, it turns out that 1∕4 of the numbers
have square roots, and each number that has a square root actually has four. Since 1 does have a square root
modulo n (itself), there are four possibilities for b: ±1 mod n and ±r mod n for some r  Z*n, r ⁄≡±1
(mod n).
Z*n, r ⁄≡±1
(mod n).
The do loop terminates if and only if b ⁄≡±1 (mod n). At that point we can factor n. Since b2 ≡ 1 (mod n), we have n∣(b2 - 1) = (b + 1)(b- 1). But since b ⁄≡±1 (mod n), n does not divide b + 1 and n does not divide b - 1. Therefore, one of the factors of n divides b + 1 and the other divides b - 1. Hence, gcd(b - 1,n) is a non-trivial factor of n.
It can be shown that there is at least a 0.5 probability that b ⁄≡±1 (mod n) for the b computed by this
algorithm in response to a randomly chosen a  Z*n. Hence, the expected number of iterations of the do
loop is at most 2. (See Evangelos Kranakis, Primality and Cryptography, Theorem 5.1 for
details.)
Z*n. Hence, the expected number of iterations of the do
loop is at most 2. (See Evangelos Kranakis, Primality and Cryptography, Theorem 5.1 for
details.)
Here’s a simple example of the use of this algorithm. Suppose n = 5 × 11 = 55, e = 3, and d = 27. (These are possible RSA values since φ(n) = 40 and ed = 81 ≡ 1 (mod 40).) Then ed - 1 = 80 = (1010000)2, so s = 4 and t = 5.
Now, suppose we take a = 2. We compute the sequence of b’s as follows:
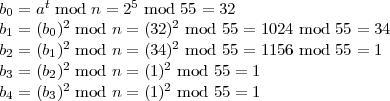
Since the last bi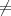 1 in this sequence is 34, and 34 ⁄≡-1 (mod 55), then 34 is a non-trivial square root of
1 modulo 55. It follows that gcd(34 - 1,55) = 11 is a prime divisor of n.
1 in this sequence is 34, and 34 ⁄≡-1 (mod 55), then 34 is a non-trivial square root of
1 modulo 55. It follows that gcd(34 - 1,55) = 11 is a prime divisor of n.
Eve isn’t really interested in factoring n, computing φ(n), or finding d, except as a means to read Alice’s secret messages. Hence, the problem we would like to be hard is the problem of computing the plaintext m given an RSA public key (n,e) and a ciphertext c. The above shows that this problem is no harder than factoring n, computing φ(n), or finding d, but it does not rule out the possibility of some clever way of decrypting messages without actually finding the decryption key. Perhaps there is some feasible probabilistic algorithm that finds m with non-negligible probability, maybe not even for all ciphertexts c but for some non-negligible fraction of them. Such a method would “break” RSA and render it useless in practice. No such algorithm has been found, but neither has the possibility been ruled out, even under the assumption that the factoring problem itself is hard.