
YALE UNIVERSITY
DEPARTMENT OF COMPUTER SCIENCE
| CPSC 467a: Cryptography and Computer Security | Handout #11 (rev. 2) | |
| Xueyuan Su | October 27, 2008 | |
Solution to Problem Set 3
Due on Wednesday, October 22, 2008.
In the problems below, “textbook” refers to Douglas R. Stinson, Cryptography: Theory and Practice, Third Edition, Chapman & Hall/CRC, 2006.
Textbook, problem 3.2.
Solution:
In each stage of the Feistel netowrk, it works as follows:
After applying n stages of the Feistel network to the plaintext L0 and R0 with the key schedule K0, ,Kn-1, we get the ciphertext Ln and Rn.
,Kn-1, we get the ciphertext Ln and Rn.
Now we show that the decryption can be done by applying the same encryption algorithm to Ln and
Rn, with the reversed key schedule Kn-1, ,K0. Switching the two sides of (1) and applying
(⊕f(Ri,Ki)) to both sides of (2), we get
,K0. Switching the two sides of (1) and applying
(⊕f(Ri,Ki)) to both sides of (2), we get
 ,K0, we get L0 and R0 at the
end.
,K0, we get L0 and R0 at the
end.
Problem 2: DES Complementation Property
Textbook, problem 3.3.
Solution:
y = DES(x,K) and y′ = DES(c(x),c(K)). The heart of DES is the Feistel network, whose one stage algorithm is described by (1) and (2). For DES(L0R0,K), define L0′ = c(L0), R0′ = c(R0) and Ki′ = c(Ki), which leads to another instance DES(L0′R0′,K′). We will show that for any stage of the Feistel network, Li′ = c(Li) and Ri′ = c(Ri).
For instance DES(L0R0,K),
For instance DES(L0′R0′,K′), Since f(Ri,Ki) uses the bitwise ⊕ operation to combine input bits of Ri (after expansion) and Ki before the permutation in S-boxes, and ⊕ operation is associative and commutative,
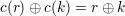 | (9) |
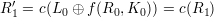 | (10) |
For instance DES(L0R0,K),
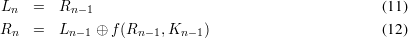
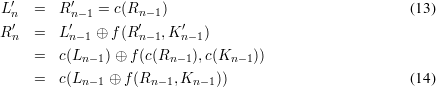
Therefore, after 16 stages of Feistel network, we can get L16′ = c(L16) and R16′ = c(R16). Concatenating L16′ and R16′, we conclude
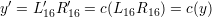 | (15) |
Textbook, problem 3.11(a). [Omit part (b).]
Solution:
Each S-box Si maps an input of six bits to an output of four bits, i.e., Si : {0,1}6 →{0,1}4. Si can be depicted by a 4 × 16 array whose entries are integers in the range [0,15]. Given a six-bit input B = b0b1b2b3b4b5, we compute Si(B) as follows. The two bits b0b5 determine the binary representation of a row r of Si, where 0 ≤ r ≤ 3, while the four bits b1b2b3b4 determine the binary representation of a column c of Si, where 0 ≤ c ≤ 15. Then we find the entry corresponding to row r and column c of the 4 × 16 array, and use it binary representation as the four-bit output.
For the special property of S4, we need to check the binary representation of each entry one by one. For example, the first entry of the second row is (13)10 = (1101)2, and the first entry of the first row is (7)10 = (0111)2. Applying the mapping, we have
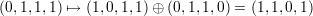 | (16) |
We put the results for all the 16 entries in the table below.
| c | first row | mapping | second row |
| 0 | (7)10 = (0111)2 | (0,1,1,1) (1,0,1,1) ⊕ (0,1,1,0) = (1,1,0,1) (1,0,1,1) ⊕ (0,1,1,0) = (1,1,0,1) | (13)10 = (1101)2 |
| 1 | (13)10 = (1101)2 | (1,1,0,1) (1,1,1,0) ⊕ (0,1,1,0) = (1,0,0,0) (1,1,1,0) ⊕ (0,1,1,0) = (1,0,0,0) | (8)10 = (1000)2 |
| 2 | (14)10 = (1110)2 | (1,1,1,0) (1,1,0,1) ⊕ (0,1,1,0) = (1,0,1,1) (1,1,0,1) ⊕ (0,1,1,0) = (1,0,1,1) | (11)10 = (1011)2 |
| 3 | (3)10 = (0011)2 | (0,0,1,1) (0,0,1,1) ⊕ (0,1,1,0) = (0,1,0,1) (0,0,1,1) ⊕ (0,1,1,0) = (0,1,0,1) | (5)10 = (0101)2 |
| 4 | (0)10 = (0000)2 | (0,0,0,0) (0,0,0,0) ⊕ (0,1,1,0) = (0,1,1,0) (0,0,0,0) ⊕ (0,1,1,0) = (0,1,1,0) | (6)10 = (0110)2 |
| 5 | (6)10 = (0110)2 | (0,1,1,0) (1,0,0,1) ⊕ (0,1,1,0) = (1,1,1,1) (1,0,0,1) ⊕ (0,1,1,0) = (1,1,1,1) | (15)10 = (1111)2 |
| 6 | (9)10 = (1001)2 | (1,0,0,1) (0,1,1,0) ⊕ (0,1,1,0) = (0,0,0,0) (0,1,1,0) ⊕ (0,1,1,0) = (0,0,0,0) | (0)10 = (0000)2 |
| 7 | (10)10 = (1010)2 | (1,0,1,0) (0,1,0,1) ⊕ (0,1,1,0) = (0,0,1,1) (0,1,0,1) ⊕ (0,1,1,0) = (0,0,1,1) | (3)10 = (0011)2 |
| 8 | (1)10 = (0001)2 | (0,0,0,1) (0,0,1,0) ⊕ (0,1,1,0) = (0,1,0,0) (0,0,1,0) ⊕ (0,1,1,0) = (0,1,0,0) | (4)10 = (0100)2 |
| 9 | (2)10 = (0010)2 | (0,0,1,0) (0,0,0,1) ⊕ (0,1,1,0) = (0,1,1,1) (0,0,0,1) ⊕ (0,1,1,0) = (0,1,1,1) | (7)10 = (0111)2 |
| 10 | (8)10 = (1000)2 | (1,0,0,0) (0,1,0,0) ⊕ (0,1,1,0) = (0,0,1,0) (0,1,0,0) ⊕ (0,1,1,0) = (0,0,1,0) | (2)10 = (0010)2 |
| 11 | (5)10 = (0101)2 | (0,1,0,1) (1,0,1,0) ⊕ (0,1,1,0) = (1,1,0,0) (1,0,1,0) ⊕ (0,1,1,0) = (1,1,0,0) | (12)10 = (1100)2 |
| 12 | (11)10 = (1011)2 | (1,0,1,1) (0,1,1,1) ⊕ (0,1,1,0) = (0,0,0,1) (0,1,1,1) ⊕ (0,1,1,0) = (0,0,0,1) | (1)10 = (0001)2 |
| 13 | (12)10 = (1100)2 | (1,1,0,0) (1,1,0,0) ⊕ (0,1,1,0) = (1,0,1,0) (1,1,0,0) ⊕ (0,1,1,0) = (1,0,1,0) | (10)10 = (1010)2 |
| 14 | (4)10 = (0100)2 | (0,1,0,0) (1,0,0,0) ⊕ (0,1,1,0) = (1,1,1,0) (1,0,0,0) ⊕ (0,1,1,0) = (1,1,1,0) | (14)10 = (1110)2 |
| 15 | (15)10 = (1111)2 | (1,1,1,1) (1,1,1,1) ⊕ (0,1,1,0) = (1,0,0,1) (1,1,1,1) ⊕ (0,1,1,0) = (1,0,0,1) | (9)10 = (1001)2 |
Read pages 3–4 of textbook and then work the following:
Solution:
By the division theorem, a = m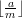 + (a mod m). Therefore, we have
+ (a mod m). Therefore, we have
Because a ⁄≡ 0 (mod m), it is easy to see that 0 < a mod m < m, which implies 0 < m - (a mod m) < m. Therefore, we have
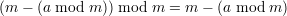 | (18) |
Combining (17) and (18), we reach the conclusion that
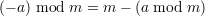 | (19) |
By definition, a ≡ b (mod m) ⇔ m∣(a - b). By the division theorem,
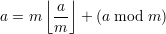 | (20) |
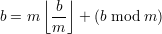 | (21) |
. Subtracting (21) from (20) gives
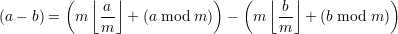 | (22) |
Together with the fact that m∣(mu + v) iff m∣v, we have
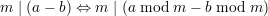 | (23) |
Because (i mod m)  Zm, m∣(a mod m-b mod m) iff a mod m = b mod m. In sum, we have
shown
Zm, m∣(a mod m-b mod m) iff a mod m = b mod m. In sum, we have
shown
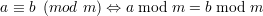 | (24) |
By the division theorem, a = km + b, where 0 ≤ b < m. It is obvious b = a mod m. Dividing both
sides of the first equation by m, we have 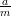 = k +
= k + 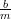 . 0 ≤ b < m implies that 0 ≤
. 0 ≤ b < m implies that 0 ≤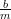 < 1, and thus
k is the largest integer that is less than or equal to
< 1, and thus
k is the largest integer that is less than or equal to 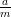 , which is precisely the definition of
, which is precisely the definition of 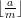 .
Therefore,
.
Therefore,
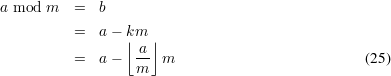
Problem 5: Extended Euclidean Algorithm
Textbook, problem 5.3. Show your work.
Solution:
a) 17-1 mod 101 = 6
| i | ri | ui | vi | qi |
| 1 | 101 | 1 | 0 | |
| 2 | 17 | 0 | 1 | 5 |
| 3 | 16 | 1 | -5 | 1 |
| 4 | 1 | -1 | 6 | 16 |
b) 357-1 mod 1234 = 1234 - 159 = 1075
| i | ri | ui | vi | qi |
| 1 | 1234 | 1 | 0 | |
| 2 | 357 | 0 | 1 | 3 |
| 3 | 163 | 1 | -3 | 2 |
| 4 | 31 | -2 | 7 | 5 |
| 5 | 8 | 11 | -38 | 3 |
| 6 | 7 | -35 | 121 | 1 |
| 7 | 1 | 46 | -159 | |
c) 3125-1 mod 9987 = 1844
| i | ri | ui | vi | qi |
| 1 | 9987 | 1 | 0 | |
| 2 | 3125 | 0 | 1 | 3 |
| 3 | 612 | 1 | -3 | 5 |
| 4 | 65 | -5 | 16 | 9 |
| 5 | 27 | 46 | -147 | 2 |
| 6 | 11 | -97 | 310 | 2 |
| 7 | 5 | 240 | -767 | 2 |
| 8 | 1 | -577 | 1844 | |
Problem 6: Linear Diophantine Equations
Textbook, problem 5.4. Show your work.
Solution:
gcd(57,93) = 3
| a | b |
| 93 | 57 |
| 57 | 36 |
| 36 | 21 |
| 21 | 15 |
| 15 | 6 |
| 6 | 3 |
| 3 | 0 |
s = -13, t = 8
| i | ri | ui | vi | qi |
| 1 | 19 | 1 | 0 | |
| 2 | 31 | 0 | 1 | 0 |
| 3 | 19 | 1 | 0 | 1 |
| 4 | 12 | 1 | 0 | 1 |
| 5 | 7 | 2 | -1 | 1 |
| 6 | 5 | -3 | 2 | 1 |
| 7 | 2 | 5 | -3 | 2 |
| 8 | 1 | -13 | 8 | |
[This is problem 6.8.2 from Trapp & Washington, “Introduction to Cryptography with Coding Theory, Second Edition”, Pearson Prentice Hall, 2006.]
Suppose your RSA modulus is n = 55 = 5 × 11 and your encryption exponent is e = 3.
Solution:
(a) Since n = 55 = 5 × 11, we have ϕ(n) = (5 - 1) × (11 - 1) = 40. Now we apply the Extended Euclidean algorithm to find d given that e = 3.
| i | ri | ui | vi | qi |
| 1 | 40 | 1 | 0 | |
| 2 | 3 | 0 | 1 | 13 |
| 3 | 1 | 1 | -13 | |
Therefore, we have d = 40 - 13 = 27.
(b) The question asks us to prove m ≡ c27 (mod 55), given c ≡ m3 (mod 55) and gcd(m,55) = 1. Starting from the first condition, we have
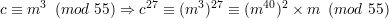 | (26) |
Euler’s theorem says, if gcd(x,n) = 1, then
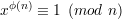 | (27) |
Since ϕ(55) = 40 and gcd(m,55) = 1, combining (26) and (27) gives
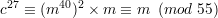 | (28) |
Because congruence is commutative, (28) implies
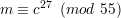 | (29) |