YALE UNIVERSITY
DEPARTMENT OF COMPUTER SCIENCE
| CPSC 467a: Cryptography and Computer Security | Handout #20 | |
| Xueyuan Su | December 11, 2008 | |
Solution to Problem Set 6
Due before midnight on Wednesday, December 3, 2008.
In the problems below, “textbook” refers to Douglas R. Stinson, Cryptography: Theory and Practice, Third Edition, Chapman & Hall/CRC, 2006.
Problem 1: ElGamal Ciphertext Decryption
Textbook, problem 6.9. An electronic copy of Table 6.3 has been placed on the Zoo in file /c/cs467/assignments/ps6/stinson_table_6.3.txt so that you don’t have to type in all of this input data. Although you will have to implement ElGamal decryption in order to solve this problem, the numbers are all small enough so that you can get by with 32-bit arithmetic rather than using one of the big number packages.
Solution:
Given p = 31847 and a = 7899, using the decryption function on page 235 in the textbook
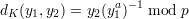 | (1) |
gives the following (formatted) plain text: “She stands up in the garden where she has been working and looks into the distance. She has sensed a change in the weather. There is another gust of wind, a buckle of noise in the air, and the tall cypresses sway. She turns and moves uphill towards the house. Climbing over a low wall, feeling the first drop of rain on her bare arms, she crosses the loggia and quickly enters the house.”
Textbook, problem 7.3(a).
Solution:
Conforming to the notation we have been used in the class, we have ki+1 = (ki + 2) mod ϕ(p) in this problem. According to the signing function, we have
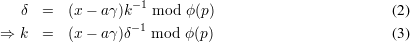
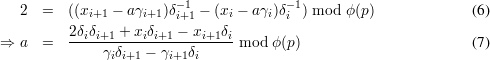
Problem 3: Simplified Feige-Fiat Authentication Protocol
Bob is using 20 rounds of the simplified Feige-Fiat authentication protocol presented in section 95 in Lecture Notes 20, thinking that the chance of an impostor successfully impersonating the legitimate Alice is only 2-20. Unbeknownst to him, there is a bug in the random number generator that he is using to generate b, so prob[b = 1] = 0.9 and prob[b = 0] = 0.1.
Solution: