YALE UNIVERSITY
DEPARTMENT OF COMPUTER SCIENCE
| CPSC 467a: Cryptography and Computer Security | Notes 15 (rev. 2) | |
| Professor M. J. Fischer | October 29, 2008 | |
Lecture Notes 15
An integer a is called a quadratic residue (or perfect square) modulo n if a ≡ b2 (mod n) for some integer b. Such a b is said to be a square root of a modulo n. We let
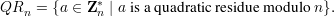
be the set of quadratic residues in Z*n, and we denote the set of non-quadratic residues in Z*n by QNRn = Z*n - QRn.
Claim 1 For an odd prime p, every a  QRp has exactly two square roots in Z*p, and exactly 1/2
of the elements of Z*p are quadratic residues.
QRp has exactly two square roots in Z*p, and exactly 1/2
of the elements of Z*p are quadratic residues.
For example, take p = 11. The following table shows all of the elements of Z*11 and their squares.
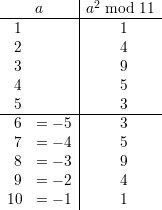
Thus, we see that QR11 = {1,3,4,5,9} and QNR11 = {2,6,7,8,10}.
Proof: We now prove Claim 1. Consider the mapping sq : Z*p → QRp defined by b b2 mod p.
We show that this is a 2-to-1 mapping from Z*p onto QRp.
b2 mod p.
We show that this is a 2-to-1 mapping from Z*p onto QRp.
Let a  QRp, and let b2 ≡ a (mod p) be a square root of a. Then -b is also a square root of a,
and b ⁄≡-b (mod p) since p ~ ∣ 2b. Hence, a has at least two distinct square roots (mod n). Now
let c be any square root of a.
QRp, and let b2 ≡ a (mod p) be a square root of a. Then -b is also a square root of a,
and b ⁄≡-b (mod p) since p ~ ∣ 2b. Hence, a has at least two distinct square roots (mod n). Now
let c be any square root of a.
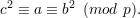
Then p∣c2 - b2, so p∣(c - b)(c + b). Since p is prime, then either p∣(c - b), in which case c ≡ b
(mod p), or p∣(c + b), in which case c ≡ -b (mod p). Hence c ≡ ±b (mod p). Since c was an
arbitrary square root of a, it follows that ±b are the only two square roots of a. Hence, sq() is a
2-to-1 function, and |QRp| = 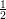 |Z*p| as desired. __
|Z*p| as desired. __
Claim 2 Let n = pq for p, q distinct odd primes. Then every a  QRn has exactly four square
roots in Z*n, and exactly 1/4 of the elements of Z*n are quadratic residues.
QRn has exactly four square
roots in Z*n, and exactly 1/4 of the elements of Z*n are quadratic residues.
Proof: Consider the mapping sq : Z*n → QRn defined by b b2 mod n. We show that this is a
4-to-1 mapping from Z*n onto QRn.
b2 mod n. We show that this is a
4-to-1 mapping from Z*n onto QRn.
Let a  QRn and let b2 ≡ a (mod n) be a square root of a. Then also b2 ≡ a (mod p)
and b2 ≡ a (mod q), so b is a square root of a (mod p) and b is a square root of a (mod q).
Conversely, if bp is a square root of a (mod p) and bq is a square root of a (mod q), then by
the Chinese Remainder theorem, the unique number b
QRn and let b2 ≡ a (mod n) be a square root of a. Then also b2 ≡ a (mod p)
and b2 ≡ a (mod q), so b is a square root of a (mod p) and b is a square root of a (mod q).
Conversely, if bp is a square root of a (mod p) and bq is a square root of a (mod q), then by
the Chinese Remainder theorem, the unique number b  Z*n such that b ≡ bp (mod p) and
b ≡ bq (mod q) is a square root of a (mod n). Since a has two square roots mod p and two square
roots mod q, it follows that a has four square roots mod n. Thus, sq() is a 4-to-1 function, and
|QRn| =
Z*n such that b ≡ bp (mod p) and
b ≡ bq (mod q) is a square root of a (mod n). Since a has two square roots mod p and two square
roots mod q, it follows that a has four square roots mod n. Thus, sq() is a 4-to-1 function, and
|QRn| = 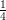 |Z*n| as desired. __
|Z*n| as desired. __
There is a simple test due to Euler for whether a number is in QRp for p prime.
Proof: Let a ≡ b2 (mod p) for some b ⁄≡ 0 (mod p). Then
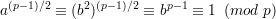
by Euler’s theorem, as desired.
For the other direction, suppose a(p-1)∕2 ≡ 1 (mod p). Clearly a ⁄≡ 0 (mod p). We show that a is a quadratic residue by finding a square root b modulo p.
Let g be a primitive root of p. Choose k so that a ≡ gk (mod p), and let ℓ = (p - 1)k∕2. Then
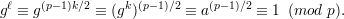
Because g is a primitive root, gℓ ≡ 1 (mod p) implies that ℓ is a multiple of p - 1. Hence, (p - 1)∣(p - 1)k∕2, from which we conclude that 2|k and k∕2 is an integer. Let b = gk∕2. Then b2 ≡ gk ≡ a (mod p), so b is a square root of a modulo p, as desired. __
The Euler criterion lets us test membership in QRp for prime p, but it doesn’t tell us how to find square roots. In case p ≡ 3 (mod 4), there is an easy algorithm for finding the square roots of any member of QRp.
Claim 4 Let p ≡ 3 (mod 4), a  QRp. Then b = a(p+1)∕4 is a square root of a (mod p).
QRp. Then b = a(p+1)∕4 is a square root of a (mod p).
Proof: Under the assumptions of the claim, p + 1 is divisible by 4, so (p + 1)∕4 is an integer. Then
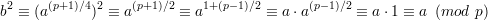
by the Euler Criterion (Claim 3). __
Let p be an odd prime. Let s and t be unique integers such that p - 1 = 2st and t is odd. (Note that s is simply the number of trailing 0’s in the binary expansion of p - 1, and t is what remains when p - 1 is shifted right by s places.) Because p is odd, p - 1 is even, so s ≥ 1.
In the special case when s = 1, p- 1 = 2t, so p = 2t + 1. Writing the odd number t as 2ℓ + 1 for some integer ℓ, we have p = 2(2ℓ + 1) + 1 = 4ℓ + 3, so p ≡ 3 (mod 4). But this is exactly the special that we considered in Section 65.
We now present an algorithm that works to find square roots of quadratic residues modulo any odd prime p. Algorithm 66.1, due to D. Shanks2 , bears a strong resemblance to Algorithm 56.1 for factoring the RSA modulus given both the encryption and decryption exponents.
Let p,s,t be as above. Assume a  QRp is a quadratic residue and u
QRp is a quadratic residue and u  QNRp is a quadratic
non-residue. (We can easily find u by choosing random elements of Z*p and applying the Euler Criterion.)
The goal is to find x such that x2 ≡ a (mod p).
QNRp is a quadratic
non-residue. (We can easily find u by choosing random elements of Z*p and applying the Euler Criterion.)
The goal is to find x such that x2 ≡ a (mod p).
The congruence x2 ≡ ab (mod p) is easily shown to be a loop invariant. It’s clearly true initially since x2 ≡ at+1 and b ≡ at (mod p). Each time through the loop, a is unchanged, b gets multiplied by t2 (lines 10 and 11), and x gets multiplied by t (line 12); hence the invariant remains true regardless of the value of t. If the program terminates, we have b ≡ 1 (mod p), so x2 ≡ a, and x is a square root of a (mod p).
To see why it terminates after at most s iterations of the loop, we look at the orders3 of b and z (mod p) at the start of each loop iteration (before line 8) and show that ord(b) < ord(z) = 2k.
On the first iteration, k = s, and z ≡ ut (mod p). We argue that ord(z) = 2s. Clearly
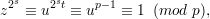
so ord(z)∣2s. By the Euler Criterion, since u is a non-residue, we have
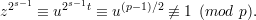
Hence, ord(z) = 2s. Using similar reasoning, since a is a quadratic residue, b2s-1 ≡ 1 (mod p), so ord(b)∣2s-1. It follows that ord(b) < ord(z) = 2s = 2k.
Now, on each iteration, line 8 sets m = ord(b) and line 9 sets t = z2k-m-1 mod p, so
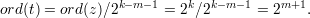
Line 10 sets z = t2, so ord(z) = ord(t)∕2 = 2m. After line 11, ord(b) < 2m. This because the old value of b and the new value of z both have order 2m. Hence, both of those numbers raised to the power 2m-1 are -1 (mod p), so their product (the new value of b) raised to that same power is (-1)2 ≡ 1. Line 13 sets k = m in preparation for the next iteration, and the loop invariant ord(b) < ord(z) = 2k is maintained. Moreover, ord(b) is reduced at each iteration, so the loop must terminate after at most s iterations.
Let n = pq, p, q distinct odd primes. We can divide the numbers in Z*n into four classes depending on their membership
in QRp and QRq.4
Let Qn11 be those numbers that are quadratic residues mod both p and q; let Qn10 be those numbers that
are quadratic residues mod p but not mod q; let Qn01 be those numbers that are quadratic residues mod q
but not mod p; and let Qn00 be those numbers that are neither quadratic residues mod p nor mod q. Under
these definitions, Qn11 = QRn and Qn00 ∪ Qn01 ∪ Qn10 = QNRn.
Fact Given a  Qn00 ∪Qn11, there is no known feasible algorithm for determining whether or not
a
Qn00 ∪Qn11, there is no known feasible algorithm for determining whether or not
a  QRn that gives the correct answer significantly more than 1/2 the time.
QRn that gives the correct answer significantly more than 1/2 the time.
The Goldwasser-Micali cryptosystem is based on this fact. The public key consist of a pair e = (n,y),
where n = pq for distinct odd primes p, q, and y  Qn00. The private key consists of p. The message space
is
Qn00. The private key consists of p. The message space
is  = {0,1}.
= {0,1}.
To encrypt m 
 , Alice chooses a random a
, Alice chooses a random a  QRn. She does this by choosing a random member of
Z*n and squaring it. If m = 0, then c = a mod n. If m = 1, then c = ay mod n. The ciphertext is
c.
QRn. She does this by choosing a random member of
Z*n and squaring it. If m = 0, then c = a mod n. If m = 1, then c = ay mod n. The ciphertext is
c.
It is easily shown that if m = 0, then c  Qn11, and if m = 1, then c
Qn11, and if m = 1, then c  Qn00. One can also show that
every element of Qn11 is equally likely to be chosen as the ciphertext c in case m = 0, and every element
of Qn00 is equally likely to be chosen as the ciphertext c in case m = 1. Eve’s problem of
determining whether c encrypts 0 or 1 is the same as the problem of distinguishing between
membership in Qn00 and Qn11, which by the above fact is believed to be hard. Anyone knowing the
private key p, however, can use the Euler Criterion to quickly determine whether or not c is
a quadratic residue mod p and hence whether c
Qn00. One can also show that
every element of Qn11 is equally likely to be chosen as the ciphertext c in case m = 0, and every element
of Qn00 is equally likely to be chosen as the ciphertext c in case m = 1. Eve’s problem of
determining whether c encrypts 0 or 1 is the same as the problem of distinguishing between
membership in Qn00 and Qn11, which by the above fact is believed to be hard. Anyone knowing the
private key p, however, can use the Euler Criterion to quickly determine whether or not c is
a quadratic residue mod p and hence whether c  Qn11 or c
Qn11 or c  Qn00, thereby determining
m.
Qn00, thereby determining
m.