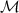 and ciphertext space
and ciphertext space 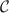 are triples of letters, encoded by numbers in the range [0..25] as with the
Caesar cipher. The key space
are triples of letters, encoded by numbers in the range [0..25] as with the
Caesar cipher. The key space 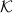 = {0,…,77}.
= {0,…,77}.
YALE UNIVERSITY
DEPARTMENT OF COMPUTER SCIENCE
| CPSC 467: Cryptography and Computer Security | Handout #5 | |
| Professor M. J. Fischer | September 25, 2017 | |
Homework Assignment 4
Due: Monday, October 2, 2017
This assignment has two parts. The goal of the first part is to test your understanding of the concepts of information leakage and perfect security. The goal of the second part is to familiarize yourself with modes of operations for block ciphers.
Problem 1: Twister
Twister is a block cipher on 3-letter blocks. It uses both substitution and transposition. The message
space 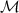 and ciphertext space
and ciphertext space 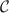 are triples of letters, encoded by numbers in the range [0..25] as with the
Caesar cipher. The key space
are triples of letters, encoded by numbers in the range [0..25] as with the
Caesar cipher. The key space 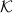 = {0,…,77}.
= {0,…,77}.
Twister encryption is the composition of two ciphers Ek1 and Ek2, so Ek = Ek2 ∘ Ek1. The first cipher,
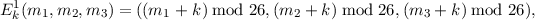
is the shift substitution used by the Caesar cipher, applied separately to each letter of the message block (m1,m2,m3). The second cipher,
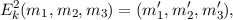
is a transposition cipher, where the letter in position j is moved to position tk(j), where tk(j) = ((j + k - 1) mod 3) + 1. Thus, m′tk(j) = mj,
Please answer questions 3 and 4 with respect to both information leakage and to the difficulty of carrying out a brute-force attack. As usual, we assume keys are chosen uniformly at random from the key space.
___________________________________________________________________________________
Problem 2: Modes of operations
CBC (block chaining) and CTR (counter mode) are the two most commonly used modes of operations for block ciphers. Both modes are explained in detail in Chapter 5 of “Understanding Cryptography” by Paar and Pelzl.