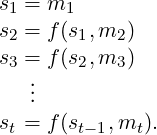| Happy | Bob | ||
| 1. |  | Choose random string r. | |
| 2. | Compute s = S(r) ⊕ h(m ⊕ r) |  | Check V (r,s ⊕ h(m ⊕ r)). |
| If check succeeds, accept m as coming from Happy. |
YALE UNIVERSITY
DEPARTMENT OF COMPUTER SCIENCE
| CPSC 467: Cryptography and Computer Security | Handout #8 | |
| Professor M. J. Fischer | October 27, 2020 | |
Homework Assignment 7
Due on Wednesday, November 4, 2020
Once Happy understood ElGamal signatures, he was excited to use them for authentication. He wants to send an authenticated message m to Bob so that Bob can verify that m came from him.
Happy has an ElGamal signing key (g,p,x) and Bob has the corresponding verification key (g,p,a). We denote the signing algorithm using that key pair by S and the verification algorithm by V . Happy and Bob also have a cryptographic hash function h whose output is the same length as the signatures produced by S.
Here’s Happy’s idea. Bob sends him a fresh tag r. Happy signs r and attaches it to a hash of his message. Bob checks the tag’s signature and accepts the message.
| Happy | Bob | ||
| 1. |  | Choose random string r. | |
| 2. | Compute s = S(r) ⊕ h(m ⊕ r) |  | Check V (r,s ⊕ h(m ⊕ r)). |
| If check succeeds, accept m as coming from Happy. |
Happy decided to build a hash function H(M) out of the AES-128 encryption function Ek. First define f(s,m) = Em(s) ⊕ m, where s and m each have length 128. Let M be a message of arbitrary length. Here’s how to compute H(M).