YALE UNIVERSITY
DEPARTMENT OF COMPUTER SCIENCE
| | CPSC 467a: Cryptography and Computer Security | Handout #18 |
| Professor M. J. Fischer | | December 7, 2006 |
|
|
|
| |
Study Guide for Final Examination
1 Exam Coverage
The final exam will cover the entire course but with greater emphasis on the topics of lectures 14–24 that
were not covered by the midterm exam. The course content is presented in several different
formats:
- In-person class lectures.
- Written lecture notes, available on the course web site.
- Written handouts, available on the course web site. I draw your attention to the four handouts on the
more mathematical aspects of the course:
- Textbook (Trappe and Washington), relevant sections from chapters 8–10, 12–14.
- Supplementary textbook (Talbot and Welsh), sections 6.1–6.3, relevant sections from chapters
8–11.
- Other resources available in the library and on the web.
- Problem sets and solutions.
2 Review Outline
Below I give a list of topics, concepts, definitions, theorems, algorithms, and protocols that we have
covered and that I expect you to know. This list is not inclusive, as I’m sure I have missed some
things.
- Digital signatures.
- Definition of a digital signature.
- Signature.
- Authenticated (signed) message.
- Signature function.
- Verification predicate.
- RSA digital signature scheme.
- Commutative cryptosystems.
- Signatures from non-commutative cryptosystems.
- Security of digital signatures.
- Kinds of forgery attacks.
- Signing random messages.
- Signing message digests.
- Differences between conventional and digital signatures.
- Disavowal.
- Message digest (hash) functions.
- Desired properties.
- One-way property.
- Weak collision-free property.
- Strong collision-free property.
- Relations among properties.
- Combining signatures with encryption.
- ElGamal signature algorithm.
- Digital signature algorithm (DSA).
- Common hash functions.
- SHA–1.
- MD5.
- Extending fixed-length hash functions.
- Doubling the reduction amount.
- A general chaining method.
- Hash functions do not always look random.
- Birthday Attack.
- Birthday paradox.
- Relevance to hash functions.
- Hash from cryptosystem.
- Techniques for building hash from cryptosystem.
- Possible problems with this approach.
- Authentication using passwords.
- Passwords.
- Insecure when sent in clear.
- Bob learns Alice’s password during normal use.
- Secure password storage.
- Problems securing storage.
- Encrypted passwords.
- Dictionary attacks.
- How does it work?
- Salt.
- Why does salt help?
- Authentication while preventing impersonation.
- Challenge-response authentication protocols.
- Basic challenge-response idea.
- Security problem having Alice sign random strings.
- Attempts to patch basic protocol.
- Simplified Feige-Fiat-Shamir authentication protocol.
- Relies on difficulty of finding square roots mod n = pq.
- Alice’s secret is square root of public number.
- Simple protocol must be repeated.
- Cheating Alice.
- Must fool Bob on each of t rounds.
- Ability to answer both challenges on some round implies can compute
 .
.
- Otherwise, success probability ≤ 1∕2t.
- Cheating Bob.
- Restricted query set limits cheating Bob’s power.
- Cheating Bob only learns random quadratic residue and one square root.
- Interactive proofs.
- Secret cave protocol.
- ZKIP for graph isomorphism.
- Graph isomorphism.
- Isomorphism problem.
- Prover (Alice).
- Verifier (Bob).
- Why doesn’t Bob learn Alice’s s secret?
- Relationship between ZKIP and secret splitting.
- Interactive proof of graph non-isomorphism.
- Non-isomorphism problem is essentially different from isomorphism problem.
- Form of protocol is quite different.
- Probably not zero knowledge.
- Bit commitment.
- Definition.
- Commitment hides Alice’s bit.
- Alice can open her commitment.
- Alice can’t reveal incorrect value.
- Use of bit-commitment ideas in non-isomorphism protocol.
- Definition of zero knowledge via simulation.
- Zero-knowledge is property of Alice’s protocol only.
- Compares power of arbitrary algorithms:
- That interact with Alice.
- That do not interact with Alice.
- Alice’s protocol is zero knowledge if both kinds of algorithms have same power.
- Composing Zero-Knowledge Proofs.
- Serial execution.
- Preserves zero knowledge.
- Many interactions.
- Parallel execution.
- Not provably zero knowledge.
- More efficient, fewer interactions.
- Full Feige-Fiat-Shamir authentication protocol.
- Combines parallel and serial execution ideas.
- Provably zero knowledge when parallelism sufficiently restricted.
- Less bandwidth than parallel execution of simple protocol.
- Non-interactive “interactive” proofs.
- Alice simulates interactive proof; sends result to Bob.
- Bob needs assurance that Alice can’t “cook” challenge bits.
- Allows Bob to impersonate Alice to Carol by replaying proof.
- Feige-Fiat-Shamir signatures.
- Based on non-interactive version of FFS protocol.
- Uses hash function to generate query bits.
- Secret splitting.
- Splitting secret into two shares using XOR.
- Splitting secret into multiple shares.
- Definition of what a (τ,k) threshold scheme is.
- Lagrange interpolation
- Shamir’s scheme based on polynomials.
- Why fewer than τ shares give no information about secret.
- Extensions.
- Verifiable secret sharing.
- Fault tolerance.
- Bit-commitment problem.
- Terminology and concepts.
- Commitment, blob, cryptographic envelope.
- commit(b).
- open(c).
- Commitment using symmetric cryptography.
- Why one-time pad does not work for bit-commitment.
- Commitment protocol using suitable symmetric cryptosystem.
- Commitment protocol using hash functions.
- Commitment protocol using PRSG.
- Abstract bit-commitment schemes.
- Defining properties.
- Generic protocol.
- Coin-flipping problem.
- Problem definition.
- Solution using blobs.
- Locked box paradigm.
- Coin-flipping using boxes with multiple locks.
- Commutative cryptosystems.
- Definition.
- RSA variation useful for implementing electronic locked boxes.
- Security properties of the RSA variation.
- Coin-flipping protocol using commutative cryptosystems.
- Card dealing using locked boxes.
- Oblivious transfer.
- Oblivious transfer of a secret.
- The problem.
- Rabin’s protocol.
- Potential problem with Rabin’s protocol.
- Fix using zero-knowledge proof of knowledge of a square root.
- One-out-of-two oblivious transfer.
- The problem.
- Protocol using two PKS key pairs.
- Pseudorandom sequence generation.
- Concepts:
- What is a PRSG?
- Why does the seed need to be random?
- What does it mean for a string to look random?
- Blum-Blum-Shub PRSG
- Blum integers.
- BBS algorithm.
- Notions of randomness.
- Indistinguishability.
- Probabilistic polynomial time Turing machine.
- Judges.
- What it means to be a cryptographically strong PRSG.
- Next-bit prediction.
- Building a judge from a next-bit predictor.
- Previous-bit prediction.
- Construction of a next-bit predictor from a previous-bit predictor.
- Security of BBS PRSG.
- Kerberos.
- Parties involved: Trusted server, Alice, Bob.
- Uses symmetric cryptography only.
- Simplified protocol (see notes).
- Nonce.
- Timestamp.
- Lifetime.
- Ticket.
- Authenticator.
- Why is authenticator needed? Why isn’t a ticket enough?
- Security of Kerberos.
- What kinds of attacks was Kerberos designed to resist?
- What kinds of attacks is it possibly subject to?
- Practical considerations in real protocol.
- Secure shell (SSH)
- Purpose: secure communication between terminal and server.
- Asymmetric cryptography used for authentication and key exchange.
- Traffic encrypted with randomly-generated session key.
- Designed for ease of use.
- Secure socket layer (SSL)
- Encrypts traffic at the ISO transport layer.
- Basis for Transport Layer Security (TLS) protocol (compatible with SSLv3).
- Operates between peers.
- Uses X.503(v3) certificates to obtain public keys.
- Performs secure key exchange to establish a session key.
- Foundations of cryptography.
- Goal: To define carefully what “hard to compute” means.
- Negligible functions.
- Strong one-way functions.
- Functions assumed without proof to be strong one-way:
- Discrete log
- Factoring
- Theorem: Existence of strong one-way functions implies P
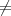 NP .
NP .
 .
.